Table of Contents
Introduction
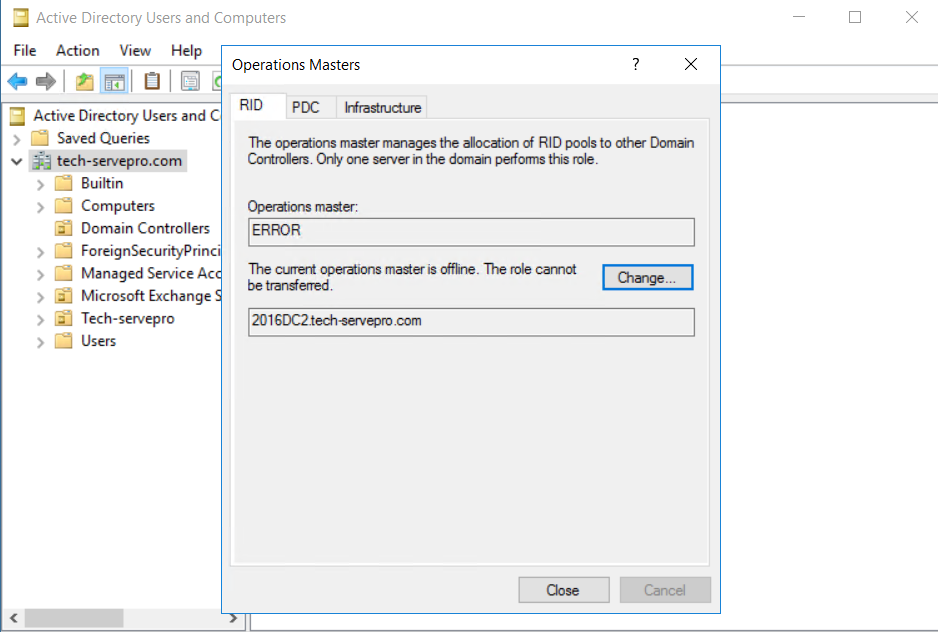
In my lab set-up, I found that the domain controllers were not syncing and I suspect it was because of the time difference between the two domain controller. On the non-PDC domain controller, I found that the operation masters were throwing an error as below.
Troubleshooting
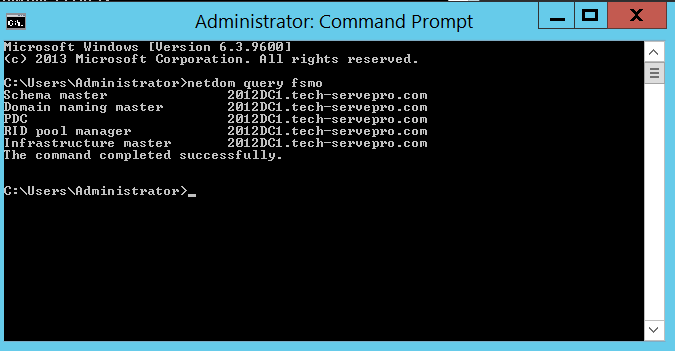
To check the FSMO role we will first run the command, and we can see DC1 is the PDC.
netdom query fsmo
dcdiag /q
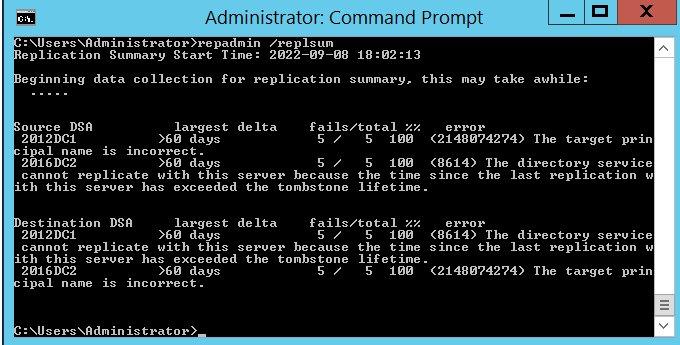
repadmin /replsum
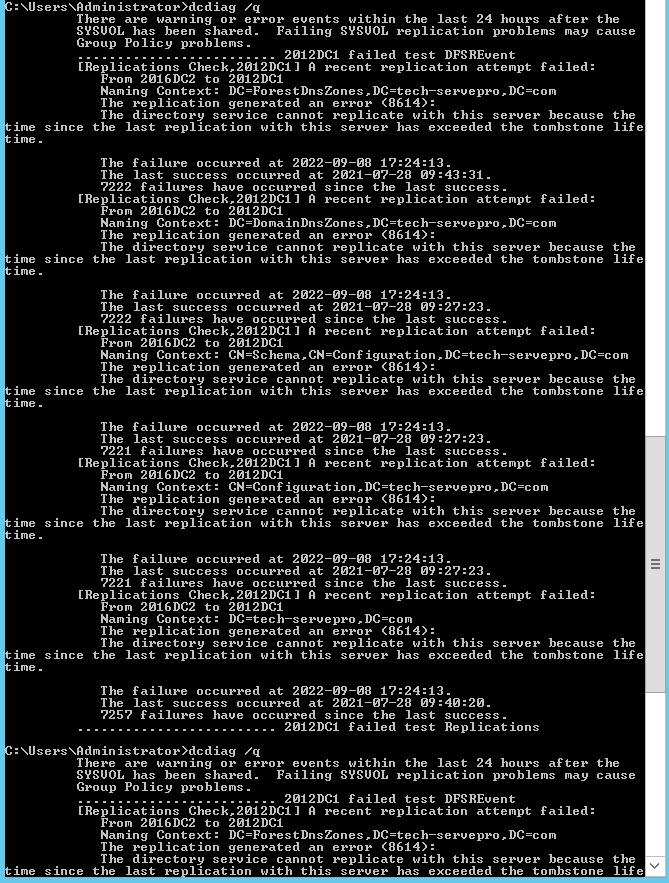
As you can see we are getting errors that the server has exceeded the tombstone lifetime and the principal name is incorrect. A tombstone is a container within Microsoft Active Directory that contains the deleted object and by default, it is 180 days. Whereas the principal name is incorrect means the secure connection between the domain controller has expired since they have not communicated for a very long time.
Resolution
Update Time Settings
First, we will check that both the domain controller have the correct time. We can sync it with an external NTP server. Once the issue is resolved we will sync the PDC with an external NTP server and all the other devices with the PDC. Run the following command on Powershell.
W32tm /config /manualpeerlist:time.windows.com /syncfromflags:manual /reliable:yes /update
W32tm /resync /rediscover
#The non-PDC will sync from PDC
w32tm /config /manualpeerlist:2012DC1 /syncfromflags:manual /update /reliable:yes
w32tm /query /configuration
w32tm /query /status
Get-Date -Format G
Update Tombstone Lifetime settings
Next, we will change the Active Directory tombstone lifetime on both the domain controllers to 730 days or 2 years which is the maximum allowable.
Open ASDI edit on the DC and right-click on connect. Choose – a well-known naming context as a configuration and then open the connection. Navigate to Configuration/Service/WindowsNT/Directory Service and right-click on properties and update the TombstoneLifetime to 730.
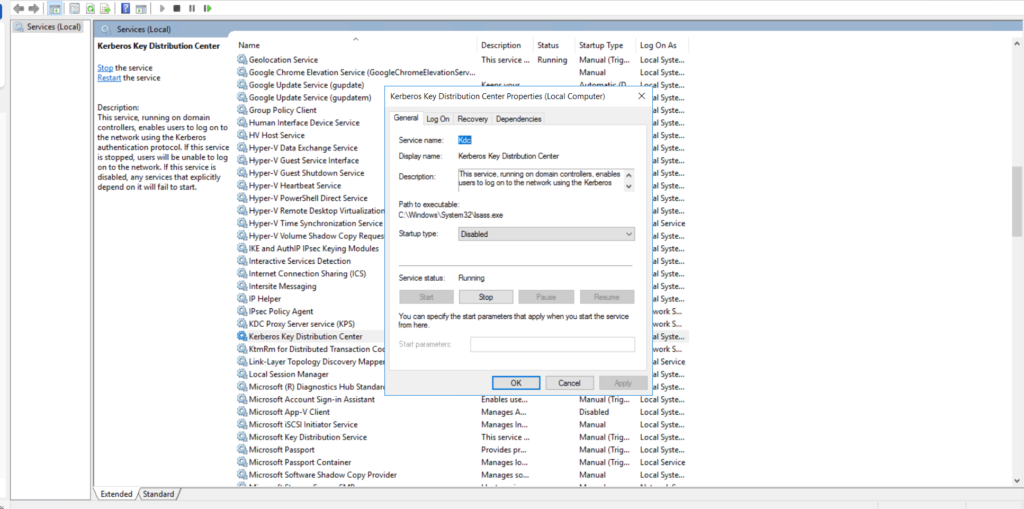
Disable Kerebros Key Distribution Center
On the domain controller having issues, open services.msc and disable Kerebros Key Distribution Center. Restart the server. Once the issue is resolved we can enable back KDC. For more information on KDC, you can check here.
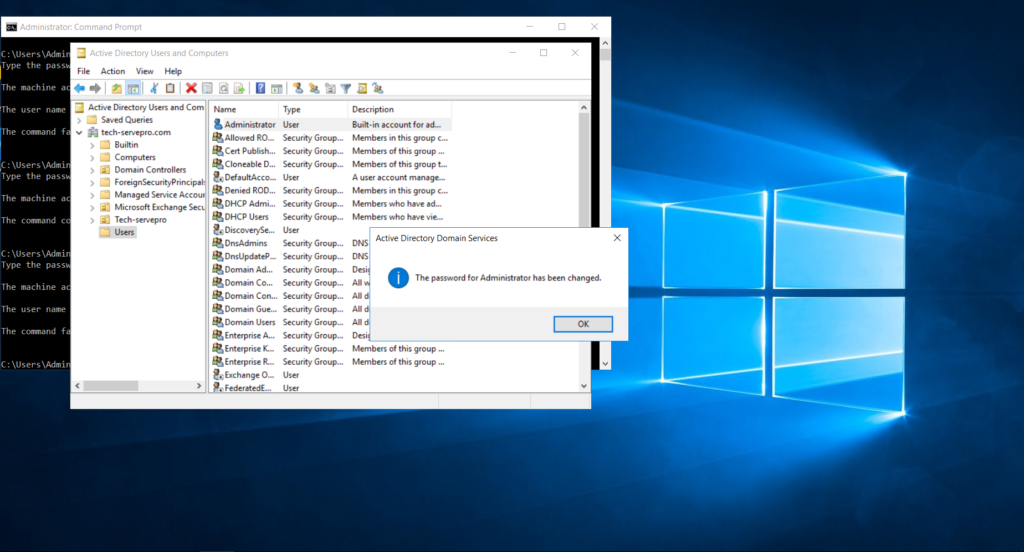
Reset administrator password
On the domain controller that is having an issue, reset the administrator password as the same password as that of the other domain controller that is running without issue.
Forceful Replication
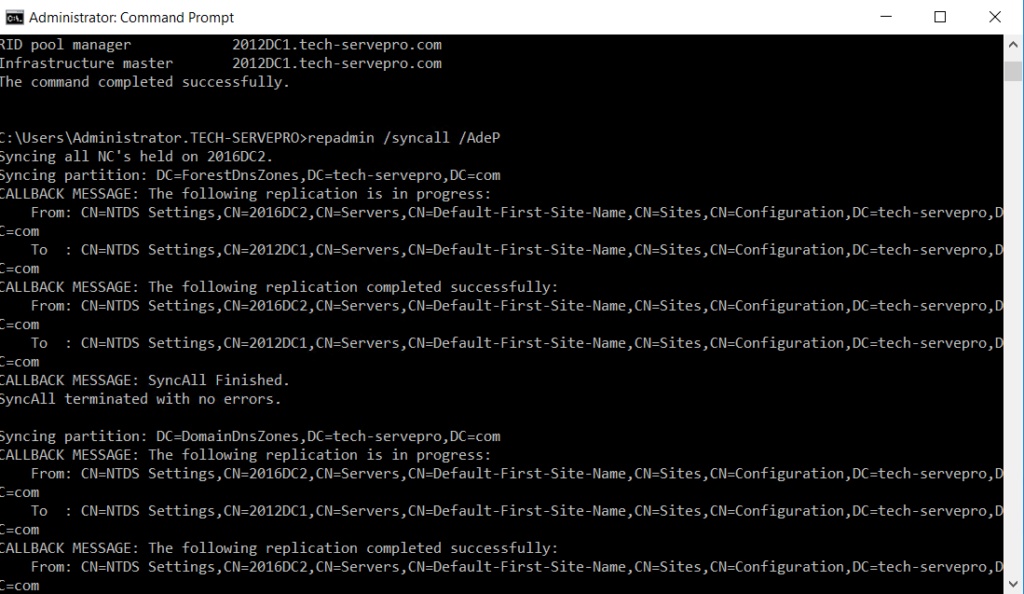
Next, we will do a forceful replication running the following command. It should run without any errors.
repadmin /syncall /AdeP
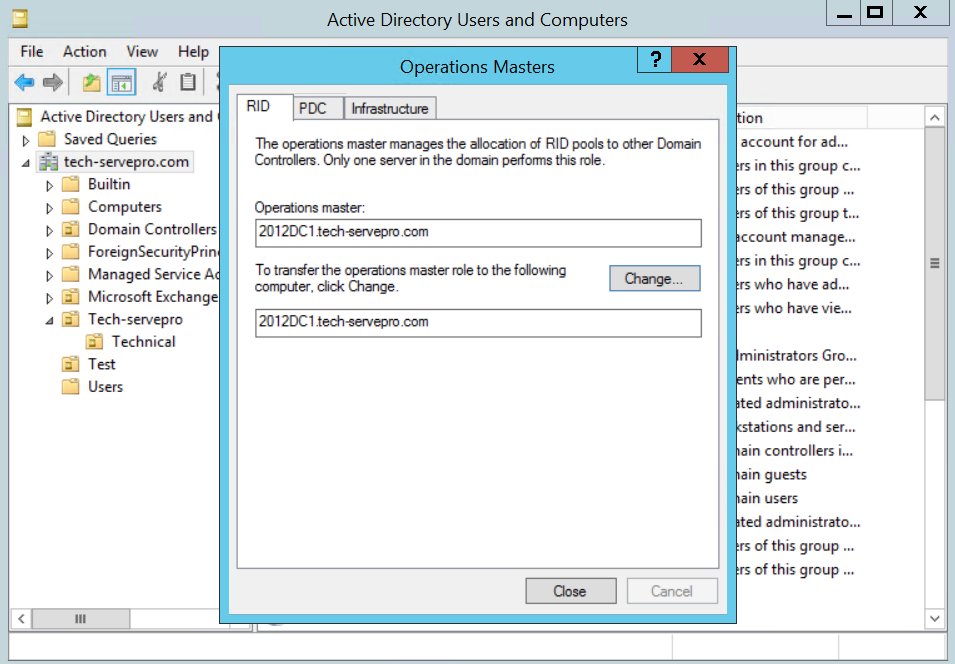
Testing out
We will check our operation master on the problematic domain controller to see if the error is resolved or not. In this case, it is resolved.
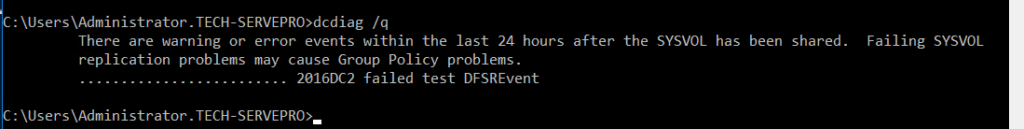
We can also run a dcdiag /q command on both the domain controllers to see if any errors.
In this case, we see the DFSREvent error, which is due to logs. It should go away after some time.
If you still have issues with replication, you can demote the problematic DC from the server manager and then add it back as a domain controller.
- KB170120